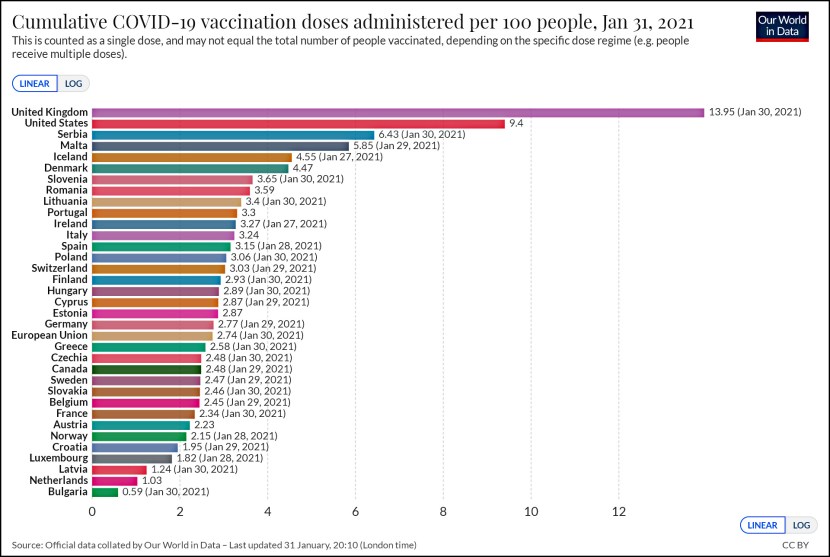
What the….? When Glenn Greenwald revealed last night that the NSA was collecting massive amounts of telephone metadata, I wasn’t surprised. I already assumed that was happening. But today he reveals details of another NSA data collection program called PRISM:
The National Security Agency has obtained direct access to the systems of Google, Facebook, Apple and other US internet giants, according to a top secret document obtained by the Guardian….The document claims “collection directly from the servers” of major US service providers.
….Companies are legally obliged to comply with requests for users’ communications under US law, but the PRISM program allows the intelligence services direct access to the companies’ servers. The NSA document notes the operations have “assistance of communications providers in the US”….With this program, the
NSA is able to reach directly into the servers of the participating companies and obtain both stored communications as well as perform real-time collection on targeted users.
I’m stumped here. How is it possible to reach “directly into the servers” of these companies? And what does that even mean? That NSA can copy anything it wants off the storage systems of these companies? That seems wildly unlikely. That NSA has tapped into incoming and outgoing communications links? That’s more plausible….I guess. I’m not sure.
For what it’s worth, Google flatly denies being a part of this. Or at least, it seems to flatly deny it:
In a statement, Google said: “Google cares deeply about the security of our users’ data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government ‘back door’ into our systems, but Google does not have a ‘back door’ for the government to access private user data.”
Would legal cooperation with PRISM done according to the law count as a “back door”? Maybe. Maybe not.
In any case, on the surface this is more mind-boggling than NSA’s surveillance of phone metadata, simply because we had no idea it was happening. Also, it appears to involve the content of communications, not just metadata.
UPDATE: The Washington Post has more:
The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio, video, photographs, e-mails, documents and connection logs that enable analysts to track a person’s movements and contacts over time.
….The PRISM program is not a dragnet, exactly. From inside a company’s data stream the NSA is capable of pulling out anything it likes, but under current rules the agency does not try to collect it all.
Analysts who use the system from a Web portal at Fort Meade key in “selectors,” or search terms, that are designed to produce at least 51 percent confidence in a target’s “foreignness.” That is not a very stringent test. Training materials obtained by the Post instruct new analysts to submit accidentally collected U.S. content for a quarterly report, “but it’s nothing to worry about.”
Even when the system works just as advertised, with no American singled out for targeting, the NSA routinely collects a great deal of American content. That is described as “incidental,” and it is inherent in contact chaining, one of the basic tools of the trade. To collect on a suspected spy or foreign terrorist means, at minimum, that everyone in the suspect’s inbox or outbox is swept in. Intelligence analysts are typically taught to chain through contacts two “hops” out from their target, which increases “incidental collection” exponentially.
….According to a separate “User’s Guide for PRISM Skype Collection,” that service can be monitored for audio when one end of the call is a conventional telephone and for any combination of “audio, video, chat, and file transfers” when Skype users connect by computer alone. Google’s offerings include Gmail, voice and video chat, Google Drive files, photo libraries, and live surveillance of search terms.
Firsthand experience with these systems, and horror at their capabilities, is what drove a career intelligence officer to provide PowerPoint slides about PRISM and supporting materials to The Washington Post in order to expose what he believes to be a gross intrusion on privacy. “They quite literally can watch your ideas form as you type,” the officer said.