 Protesters in Baniyas, Syria, on May 5 Syria-Frames-Of-Freedom/FlickrLast month, Mother Jones reported that the Syrian regime was using internet filtering technology manufactured by an American company, Blue Coat Systems, to aid in its months-long crackdown on dissidents. In the weeks following our report, the State Department and Commerce Department said they were both looking into the matter, and US senators called for congressional probes on the company.
Protesters in Baniyas, Syria, on May 5 Syria-Frames-Of-Freedom/FlickrLast month, Mother Jones reported that the Syrian regime was using internet filtering technology manufactured by an American company, Blue Coat Systems, to aid in its months-long crackdown on dissidents. In the weeks following our report, the State Department and Commerce Department said they were both looking into the matter, and US senators called for congressional probes on the company.
On October 29, Blue Coat finally admitted to the Wall Street Journal that its products had indeed been used in Syria. The company now claims that it learned about its Syria connection the same way Mother Jones did—from computer log files posted on the internet by the hacktivist group Telecomix. But just over a month ago, Blue Coat was telling a completely different story.
Tim Lord, an editor at the massively popular “news for nerds” site Slashdot, claims that Steve Schick, a spokesman for Blue Coat, emailed him a response to the Syria allegations on October 11. Asked for comment, Schick referred Mother Jones to the statement on the Blue Coat website in which the company says it learned of its devices being used in Syria from the leaked logs. Lord has provided Mother Jones with a copy of Schick’s email, a portion of which he posted to Slashdot. (You can read the email in full below.) In it, Schick writes that Blue Coat “does not provide any kind of technical support, professional services or software maintenance” to Syria and “has no evidence” its devices are being used there:
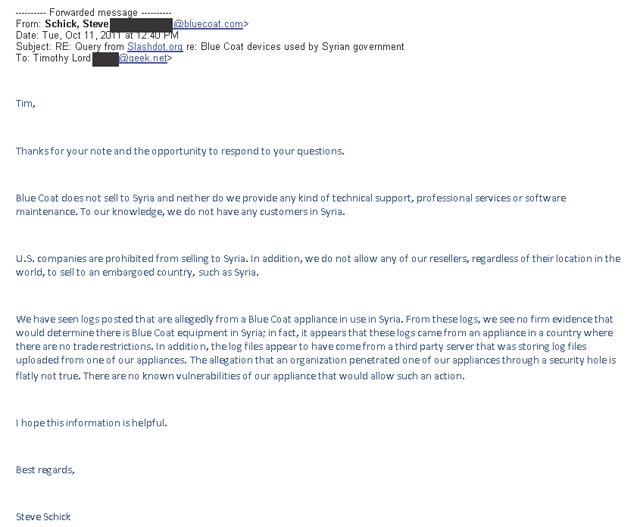
Schick’s emailed statement directly contradicts what Blue Coat said just weeks later, on October 29, when company officials told the Wall Street Journal that their devices in Syria had been transmitting automatic “heartbeat” messages back to Blue Coat. (The company claims it does not monitor those sorts of messages.) The filtering devices also had active “Blue Coat service and support contracts,” according to the Journal.
“Was Schick lying? I think so, sure, though I at least hoped he wasn’t,” Lord says. “It’s within the realm of possibility that the company was mistaken (at the time), but I doubt it.”
Bruce Schneier, a respected security analyst, says Blue Coat could have easily determined whether its devices were being used in Syria. To remain effective, internet filtering devices need regular updates and support, similar to the virus definition updates that consumers receive from computer security companies like Norton. Schneier believes the Syrian Blue Coat products would have received updates from the Silicon Valley company—especially given the fact that the devices had active service and support contracts. Blue Coat would have just had to glance at its records.
Lord still has more questions. “I’d like to know what about the logs…they could construe as supporting their former public position that [the logs] came from machines outside Syria,” he says. “It’s those logs that led Telecomix to the opposite conclusion”—a conclusion that Blue Coat now supports.












